LockMagic and Auditing
LockMagic allows for revoking the access to encrypted content. The solution allows users to set a time when access to the data is no longer allowed.
Thus, if data is sent to a customer, for evaluation purposes, LockMagic allows the user to set a specific time when the customer will no longer be able to access
the sent data. The expiry time can be set to any time zone.
However, unlike traditional methods, the time on the local computer is not checked for this functionality, thus,
changing the time on the local computer will not alter the expiry process.
LockMagic keeps a detailed audit trail of anyone that accesses data that was accessed.
Thus, if for some reason, the users’ data fell into unauthorized hands, the LockMagic server can be consulted to inform the owner of the data of the location
of the unauthorized user that accessed this data. Therefore, if a user lost data that was encrypted by LockMagic on a USB drive, or a user sent data,
via email to another recipient, when said data is accessed, Lock Magic’s audit trail can be consulted to determine the identity of the unauthorized user.
The figure B, below shows the scenario of data from locations within the United States.
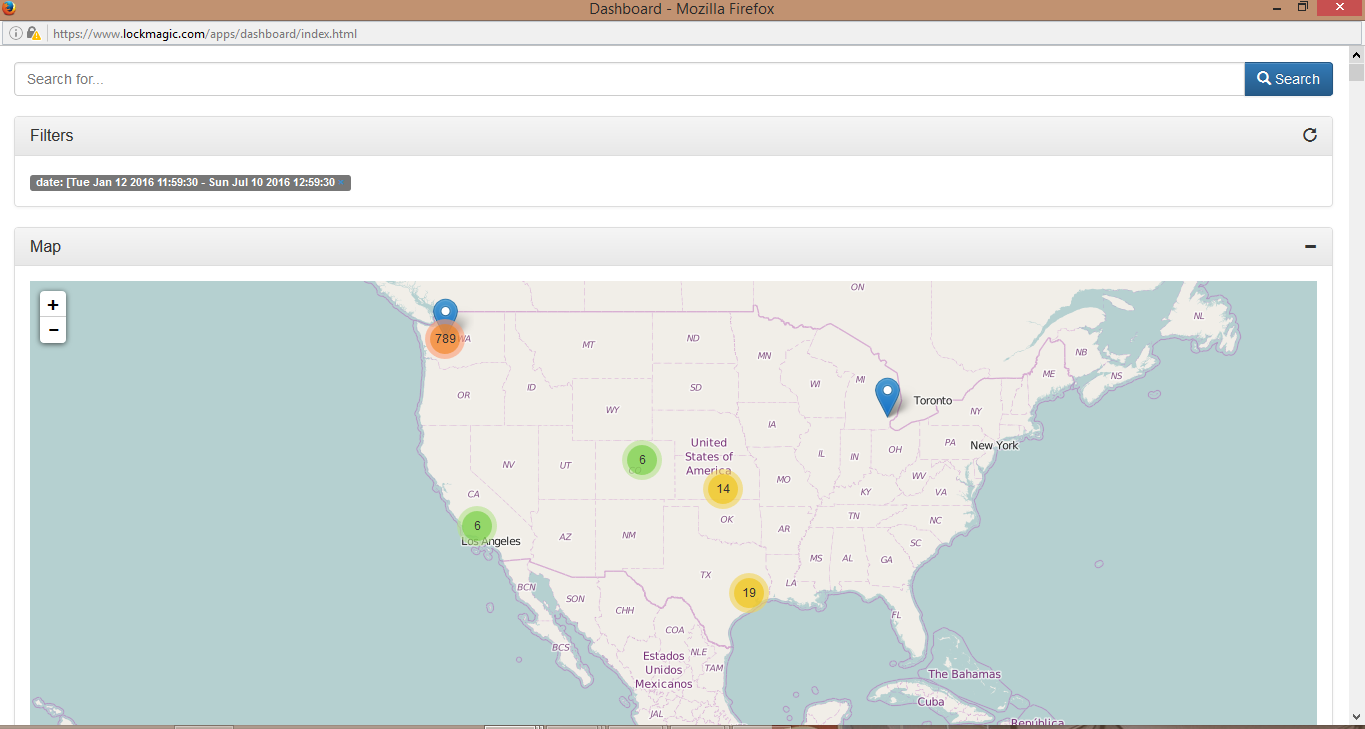
Figure B
In addition to time, LockMagic allows the user to search through the audit logs to discover alerts and expired content. The following figure illustrates alerts
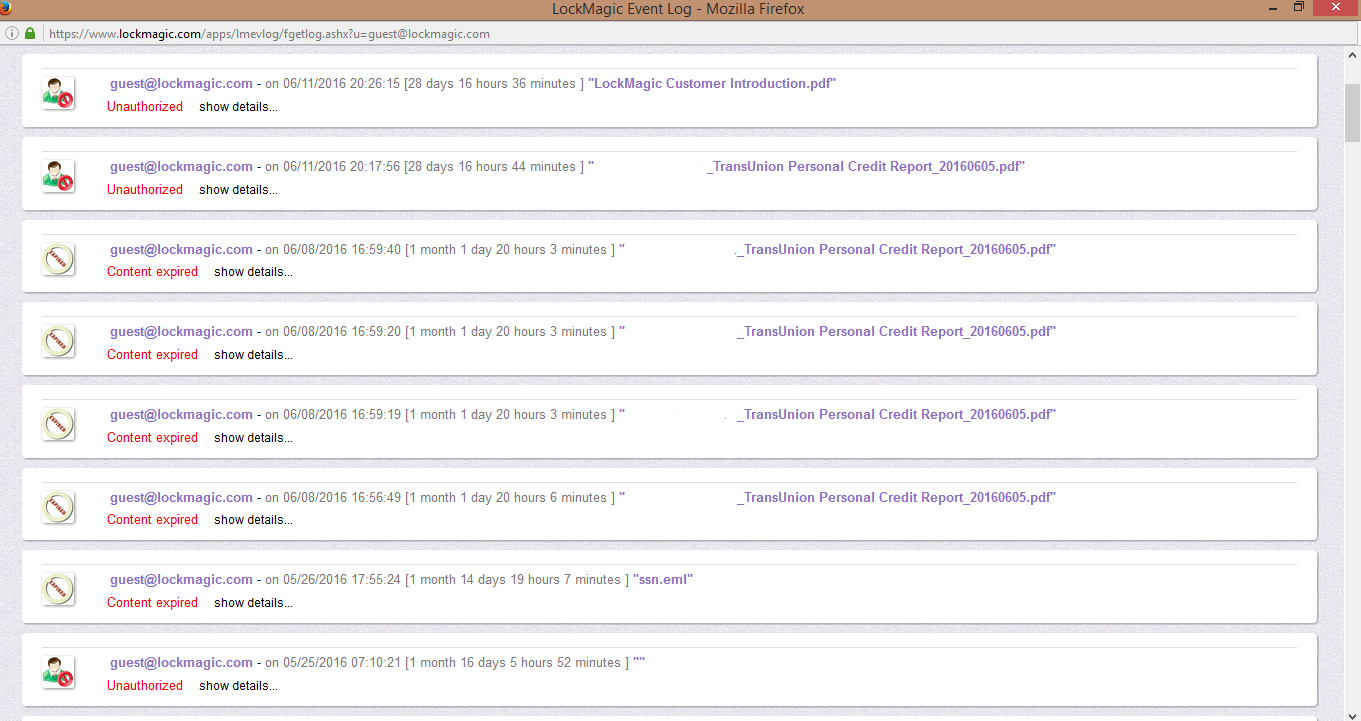
Highlights
- Detailed audit logs that enables the discovery of who has access to data
- Immediate notification of unauthorized access
- Ability to revoke access to data, on demand, based on:
- Time
- Recipient Identity
- Author Identity